
Confidential Computing has come a long way since Intel pioneered the technology in the data center almost six years ago. I recently had a chance to showcase Intel’s capabilities at the Open Confidential Computing Conference (OC3) virtual event, and how we’re enabling an emerging market opportunity: Confidential AI.
There is no bigger topic in technology right now than AI. Even if you discount all the hype, the potential to create new value with AI is enormous. However, the nature of the data powering many AI use cases brings challenges with regulations, privacy, and trust. Combining Confidential Computing capabilities with AI can harmonize ambitions for revenue growth and cost-savings with the security and privacy safeguards increasingly demanded by regulations.
With Confidential AI, we have the rare convergence of business innovation and regulatory compliance pulling together in the same direction. This alignment accelerates your time to value. Using a trusted execution environment (TEE) to protect customer data and AI models helps enable compliance with privacy and security regulations.
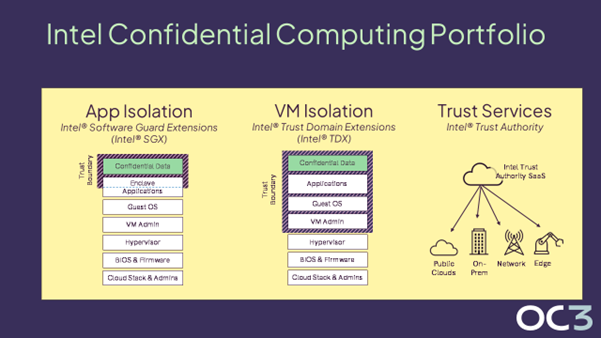
Recent advances have expanded the Intel Confidential Computing portfolio to include technologies for application isolation, VM isolation, and attestation services. This approach gives customers options to tailor their solutions to every use case.
Intel® Software Guard Extensions (Intel® SGX) is designed for scenarios requiring a smaller trusted compute base (TCB) and granular attestation down to the application level, while Intel TDX can be the optimal solution when the priority is migrating existing applications and VMs to a confidential environment, with few or no code changes. And, when the use case calls for deployment across multiple clouds or on-prem locations, Intel® Trust Authority provides unified attestation across domains.
These technologies allow you to take advantage of the emerging Confidential AI opportunity, especially when combined with AI workload accelerators like Intel® Advanced Matrix Extensions (Intel® AMX). Customers have used Intel AMX to accelerate inference while keeping results within a CPU-based TEE.
Confidential AI is just one example of how Intel helps secure and scale data privacy applications using Confidential Computing. Check out my OC3 session for more information and all other sessions here: https://intel.ly/2024OC3
---
Anand Pashupathy is Vice President and General Manager of Security Software & Services (S3) Division in the Software and Advanced Technology Group where he leads a team of senior leaders to deliver security software technologies and services that activate and differentiate silicon security features, and cultivate a high standard of security, operational & cultural excellence. Anand is also responsible for Intel’s Confidential Compute vision, strategy, and execution.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.