- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Note: This article is an English translation of this Japanese article. Please refer to the original article for updates.
Introduction
In this “Intel® FPGA Advent Calendar 2021”, various articles have highlighted the RISC-V version of the Soft CPU Core, known as the Nios® V processor (hereinafter referred to as Nios V), which is now included in Intel® Quartus® Prime Pro Edition 21.3 (hereafter QuartusPro v21.3). Along with this introduction, OpenOCD has been implemented as the debugging mechanism for Nios V. It raises the question: Could OpenOCD be used for JTAG debugging with USB Blaster, not just for Nios V but for other CPUs as well? This article explores that possibility.
The experiment conducted focused on the CPU (Arm Cortex-A9) of the Cyclone® V SoC FPGA1. This section includes the OpenOCD configuration file for connecting to the Cyclone V SoC, along with gdb debugger scripts for downloading and executing code, and a TCL script for telnet connection.
What is OpenOCD?
OpenOCD, short for Open On-Chip Debugger, is an "Open Source software aimed at providing debugging, in-system programming, and boundary-scan for embedded devices."2 It incorporates features of a gdb server and a telnet server, supporting a variety of debug probes, thereby enabling debugging on numerous embedded devices. The basic usage involves running OpenOCD as a server in the background, acting as an intermediary to facilitate connections between client software (like gdb or telnet clients) and the debug probe.
The version of OpenOCD included in QuartusPro v21.3 supports USB Blaster, allowing JTAG debugging via gdb debugger, targeting not just Nios V but potentially other CPUs as well, such as Arm Cortex-A9. This section delves into the investigation and testing of this capability.
For setting up OpenOCD, on Windows, the installation of QuartusPro v21.3 is required. On Linux, installing only the Programmer of QuartusPro v21.3 suffices for using OpenOCD. No additional installation of the Nios V toolchain is necessary. Furthermore, OpenOCD is available for use free of charge, without the need for a paid license.
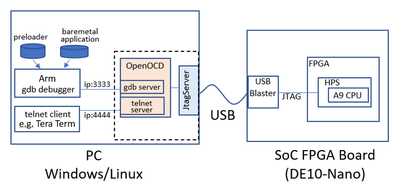
Overall Structure
This section outlines the tested configuration.
Hardware: The debugger PC and the FPGA board are connected via JTAG (actually using an OnBoard USB Blaster, so a USB cable). The PC can be either Windows or Linux.
PC Software: OpenOCD is kept running, with the gdb server accessing the USB Blaster being active. The gdb debugger for Arm CPU is connected to the OpenOCD gdb server to facilitate debugging, which includes code downloading and execution.
Board Used for Testing
The Terasic DE10-Nano kit, equipped with the Cyclone V SoC, was used for the experiment.
Launching OpenOCD
To start OpenOCD, the Nios V Command Shell from Quartus v21.3 is used.
Initially, it's necessary to verify whether the USB Blaster of the DE10-Nano kit is correctly recognized by the PC as a JTAG device and if the HPS and FPGA are detected. This involves connecting the J13 of the DE10-nano to the PC using a mini-USB cable without an SD card inserted, and then powering on the DE10-nano. Following this, the jtagconfig command is executed.
[niosv-shell] C:\intelFPGA_pro\21.3> jtagconfig
1) DE-SoC [USB-1]
4BA00477 SOCVHPS
02D020DD 5CSEBA6(.|ES)/5CSEMA6/..
If this display appears, it is normal. It confirms the JTAG ID of the HPS containing the Arm CPU as 4BA00477 (the same as in Arria10's HPS).
Creating OpenOCD Configuration File
To use OpenOCD, a configuration file detailing the target environment is required. The format adheres to TCL. Initially, reference files within the installation folder of QuartusPro v21.3 are sought. Within the folder named
<install_folder>/quartus/bin64/oocd/openocd/scripts/board
there is a file named
altera_arria10__aji_client.cfg.
It appears to be a configuration file for connecting to the HPS of Arria10 SoC, as inferred from its name and comments. Using this as a reference, a successful connection to the target Cyclone V SoC was established. The configuration file is as follows, named cyclone5_client.cfg.
###############################################################
# Point: Specify aji_client as the Driver
adapter driver aji_client
###############################################################
# Chip Name: Can be changed to any name you prefer (let's keep it as cvsoc)
set _CHIPNAME cvsoc
###############################################################
# JTAG ID of HPS TAP (Test Access Port)/DAP (Debug Access Port)
set _DAP_TAPID 0x4ba00477
###############################################################
# Declare HPS DAP as the JTAG TAP (Test Access Port)
jtag newtap $_CHIPNAME cpu -irlen 4 -expected-id $_DAP_TAPID
###############################################################
# Declare that the HPS TAP is an ARM DAP (Debug Access Port).
# Do this when ARMv6-M, ARMv7, ARMv8 are the targets
dap create $_CHIPNAME.dap -chain-position $_CHIPNAME.cpu
###############################################################
# The target to be operated by the gdb debugger will be core0 of the HPS DAP
target create $_CHIPNAME.cpu.0 cortex_a -dap $_CHIPNAME.dap -coreid 0 -dbgbase 0x80110000
After several trials and errors, the file was ultimately reduced to only the essential parts from the original Arria10 file. One addition, in the last line of target create…, is -dbgbase 0x80110003.
Launching and Verifying OpenOCD
The Nios V Command Shell of v21.3 is started. In this Shell, after changing the directory to where the cyclone5_client.cfg file was saved, execute openocd -f cyclone5_client.cfg. Subsequently, the following log appears, and then the log display stops.
[niosv-shell] C:\de10nano\OpenOCD_download> openocd -f cyclone5_client.cfg
Open On-Chip Debugger 0.11.0-R21.3
Licensed under GNU GPL v2
...[omitted for brevity]...
Info : Listening on port 4444 for telnet connections
...[omitted for brevity]...
Info : At present, The first hardware cable will be used [1 cable(s) detected]
Info : Cable 1: device_name=(null), hw_name=DE-SoC, server=(null), port=USB-1, chain_id=0000019c3ca88620, persistent_id=1, chain_type=1, features=2048, server_version_info=Version 21.1.0 Build 842 10/21/2021 SJ Standard Edition
Info : TAP position 0 (4BA00477) has 0 SLD nodes
Info : TAP position 1 (2D020DD) has 0 SLD nodes
Info : Discovered 2 TAP devices
Info : Detected device (tap_position=0) device_id=4ba00477, instruction_length=4, features=0, device_name=SOCVHPS
Info : Found a ARM device at tap_position 0. Currently assume it is JTAG-DP capable
Info : Detected device (tap_position=1) device_id=02d020dd, instruction_length=10, features=4, device_name=5CSEBA6(.|ES)/5CSEMA6/..
Info : Found an Intel device at tap_position 1.Currently assuming it is SLD Hub
Info : This adapter doesn't support configurable speed
Info : JTAG tap: cvsoc.cpu tap/device found: 0x4ba00477 (mfg: 0x23b (ARM Ltd), part: 0xba00, ver: 0x4)
Info : JTAG tap: auto0.tap tap/device found: 0x02d020dd (mfg: 0x06e (Altera), part: 0x2d02, ver: 0x0)
Warn : AUTO auto0.tap - use "jtag newtap auto0 tap -irlen 10 -expected-id 0x02d020dd"
...[omitted for brevity]...
Info : starting gdb server for cvsoc.cpu.0 on 3333
Info : Listening on port 3333 for gdb connections
From the first half of the log, it's evident that the telnet server has started, waiting for connections on port 4444. The latter half, beginning with "Info: JTAG tap:", indicates that the device ID has been correctly recognized. Furthermore, from the last two lines, it can be seen that the gdb server has been successfully launched and is waiting for connections on port 3333, confirming a successful connection to the Cyclone V HPS gdb server.
By the way, the "Warn: AUTO auto0.tap…" message that appears in between indicates that the FPGA's JTAG TAP definition was omitted in the cyclone5_client.cfg file, leading the tool to automatically detect it. The JTAG instruction length and other details are also auto-detected.
Connecting to the gdb Debugger
Now that OpenOCD has been successfully launched, the next step is to connect it with the gdb debugger.
Starting and Verifying gdb
The gdb debugger is initiated and connected to the OpenOCD gdb server. Here, the Arm gdb included with SoCEDS v18.1 standard edition is used (generally, any gdb supporting the target CPU should work, but there are concerns that if an ELF file is read by gdb, the symbol table might not be loaded correctly unless the gdb version matches the gcc toolchain that created the ELF). Several reasons for using v18.1 include:
- The sample HW design for DE10-nano compiles without issues (up to v18.1, the sample containing FrameReader Video IP can be compiled).
- There's no need to download & install Cygwin or WSL separately, among other reasons4.
The SoCEDS command shell is launched, and from there, the arm-altera-eabi-gdb for Arm is started. It's crucial to include the option for connecting to OpenOCD's gdb server on port 3333 at this stage.
arm-altera-eabi-gdb -ex 'target extended-remote localhost:3333'
$ arm-altera-eabi-gdb -ex 'target extended-remote localhost:3333'
GNU gdb (Sourcery CodeBench Lite 2016.11-88) 7.11.1.20160608-git
Copyright (C) 2016 Free Software Foundation, Inc.
...[omitted for brevity]...
Remote debugging using localhost:3333
warning: No executable has been specified and target does not support
determining executable automatically. Try using the "file" command.
0x00002fa8 in ?? ()
(gdb)
The gdb server is successfully connected on localhost:3333, and the CPU is stopped at address 0x00002fa8. This also adds a few lines of messages to the Nios V command shell that is running OpenOCD (examples are omitted here).
Next, to see if the state of the Arm CPU is visible, the info reg command is used to check.
(gdb) info reg
r0 0x0 0
r1 0x0 0
r2 0xfffffee0 4294967008
r3 0xff704000 4285546496
r4 0x77857713 2005235475
r5 0xffd02000 4291829760
r6 0x76 118
r7 0xfffff014 4294963220
r8 0xfffff014 4294963220
r9 0x76 118
r10 0xffd02000 4291829760
r11 0xffd02000 4291829760
r12 0xa0002041 2684362817
sp 0xfffffed0 0xfffffed0
lr 0x3104 0x3104
pc 0x2fa8 0x2fa8
cpsr 0x600001d3 1610613203
(gdb)
All register contents are successfully verified.
Trying the print command for system memory access is also explored. Here, the crc register of the System Manager, mapped at address 0xffd080f0, is accessed.
(gdb) print/x *0xffd080f0
$1 = 0xe763552a
(gdb)
As per the Cyclone V SoC documentation, the value is at its initial state after a cold reset, which is 0xE763552A.
This confirms that all basic gdb commands are functioning correctly!
To exit gdb, use the 'q' command. Also, terminate OpenOCD by inputting Ctrl-C.
Download and Run Script with gdb
Now, let's proceed to the final goal of this article: downloading and running code using gdb scripts. Below are some script examples, tailored to the file format and version of the preloader. Basically, converting the contents of the scripts (*.ds) provided for Arm DS (or Arm DS-5) to gdb format will suffice.
ELF Format Preloader (v2013.01)
First, a script for downloading and executing an ELF format file of the preloader version 2013.01. For a long time (until SoCEDS v18.1), the preloader (u-boot) code included with SoCEDS was of version 2013.01. The script example for downloading and executing the resulting ELF format file (spl/u-boot-spl) on the target device (DE10-Nano's Cyclone V SoC) is as follows (created as download_preloader_elf.gdb):
set confirm off
set pagination off
restore
symbol-file -readnow
thbreak spl_boot_device
jump _start
#Stop watchdog timer
#permodrst Reg , reset watch dog timer
#set $permodrst = (int *)0xffd05014
#set *$permodrst = (*$permodrst) | (1<<6)
#set *$permodrst = (*$permodrst) & ~(1<<6)
[Explanation of the Script] The key point here is setting a breakpoint at the function spl_boot_device. This function checks where the preloader will load the next Application image from (SD card or QSPI or NAND). When this point is reached, all necessary initializations for booting are completed, and the debugger stops here (further execution will result in an error as no SD card is inserted). In most cases, the next step would be to download and debug the Application. The final three lines (set ...), which are commented out, are meant to stop the WatchDog timer started by the preloader. They toggle the reset bit of the WatchDogTimer0 in the reset manager to stop WatchDogTimer0. If additional tasks, like running an Application, are to be performed afterward, the WatchDog timer, if left running, might cause a reset due to a timeout (leading to an unexpected reset). To prevent this, uncomment these last three lines.
This script is executed using the -x option with gdb.
arm-altera-eabi-gdb -ex 'target extended-remote localhost:3333' -x download_preloader_elf.gdb
Important: Before running this gdb command, please restart the DE10-Nano board5 and restart OpenOCD.
$ arm-altera-eabi-gdb -ex 'target extended-remote localhost:3333' -x download_preloader.gdb
GNU gdb (Sourcery CodeBench Lite 2016.11-88) 7.11.1.20160608-git
Copyright (C) 2016 Free Software Foundation, Inc.
License GPLv3+: GNU GPL version 3 or later <http://gnu.org/licenses/gpl.html>
...[omitted for brevity]...
Remote debugging using localhost:3333
warning: No executable has been specified and target does not support
determining executable automatically. Try using the "file" command.
0x00002fa4 in ?? ()
Restoring section .text (0xffff0000 to 0xffff6968)
Restoring section .rodata (0xffff6968 to 0xffff81f0)
Restoring section .data (0xffff81f0 to 0xffff90c4)
Hardware assisted breakpoint 1 at 0xffff1342
cvsoc.cpu.0 rev 0, partnum c09, arch f, variant 3, implementor 41
Temporary breakpoint 1, 0xffff1342 in spl_boot_device ()
(gdb)
When executing this command, if you have the DE10-Nano's serial terminal open, the following display occurs, confirming that the preloader is executed:
U-Boot SPL 2013.01.01 (Dec 14 2021 - 13:59:40)
BOARD : Altera SOCFPGA Cyclone V Board
...[omitted for brevity]...
INFO : Watchdog enabled
SDRAM: Initializing MMR registers
SDRAM: Calibrating PHY
SEQ.C: Preparing to start memory calibration
SEQ.C: CALIBRATION PASSED
SDRAM: 1024 MiB
ELF Format Preloader (v2021.04 and Later)
Preloader, based on the u-boot code, has undergone changes since version 2021.04 to include device tree files. Consequently, the debugger download script has also needed to be modified. Below is the updated script:
set confirm off
set pagination off
restore
symbol-file -readnow
restore u-boot-spl.dtb binary &__bss_end
thbreak spl_boot_device
jump _start
#Stop watchdog timer
#permodrst Reg , reset watch dog timer
#set $permodrst = (int *)0xffd05014
#set *$permodrst = (*$permodrst) | (1<<6)
#set *$permodrst = (*$permodrst) & ~(1<<6)
Explanation of the Script The new preloader (u-boot) requires loading both the ELF file and the device tree (.dtb) into memory. The line restore u-boot-spl.dtb binary &__bss_end loads the device tree. __bss_end is the end address of the preloader code, and the .dtb is placed immediately after it in memory, as per the specifications of this version of preloader (u-boot).
Binary Format Preloader-mkpimage.bin
This script is used to execute the preloader using the binary format file preloader-mkpimage.bin, intended for writing to a boot SD card. (This file comes included with the sample design DE10_NANO_SoC_GHRD folder provided by Terasic, useful for those who want a quick operational check). The script can also launch the preloader binary file u-boot-splx4.sfp, created for newer versions (later than 2013.xx) of boot media.
set confirm off
set pagination off
restore binary 0xffff0000 0x0 0xefff
watch *0xff704004
jump *0xffff004c
#Stop watchdog timer
#permodrst Reg , reset watch dog timer
#set $permodrst = (int *)0xffd05014
#set *$permodrst = (*$permodrst) | (1<<6)
#set *$permodrst = (*$permodrst) & ~(1<<6)
Explanation of the Script The key point is specifying the memory offset address (0xffff0000) for writing the binary, the start (0x0), and the end position (0xefff) of the binary file in the restore command. The memory offset address (0xffff0000) is the starting address of the HPS OnChipMemory. The start of the binary file is from the beginning (0x0), and the end is the maximum size of the preloader code, 0xefff. A watch point (triggered on specified memory access) is used to stop the preloader since it's a binary code without symbol information. The watch point is set to halt the CPU when the SD card controller is accessed for reading/writing. 0xff704004 is the address of a register in the SD card controller. The execution start address is 0xffff004c, as specified by the binary format and bootrom specifications.
Downloading and Running Preloader/Baremetal App
As a more practical example, this script loads and executes the preloader, followed by a sample Baremetal application.
set confirm off
set pagination off
restore <u-boot-splのpath>
symbol-file -readnow <u-boot-splのpath>
thbreak spl_boot_device
jump _start
#Stop watchdog timer
#permodrst Reg , reset watch dog timer
set $permodrst = (int *)0xffd05014
set *$permodrst = (*$permodrst) | (1<<6)
set *$permodrst = (*$permodrst) & ~(1<<6)
# load and run Application
restore <application elf path>
symbol-file -readnow <application elf path>
jump _start
Explanation of the Script: This script adds commands to download and execute an application ELF file (.axf) to the previously introduced script for downloading the preloader. After executing the preloader, a process to stop the WatchDog Timer is enabled. Ideally, this process to stop the WatchDog Timer should be performed at the beginning of the application. Since this process is not included in the Software Examples provided with SoCEDS, it's incorporated here. Caution When Building the Software Example Included with SoCEDS: This time, I tried compiling and verifying the operation of the Software Example included with SoCEDS v18.1, specifically the Altera-SoCFPGA-HardwareLib-16550-CV-GNU (/embedded/examples/software/Altera-SoCFPGA-HardwareLib-16550-CV-GNU). Some points to note: the original sample code is intended to be executed using an Arm debugger and is set up to display printf output on the debugger's console (using a feature called semi-hosting). With the gdb debugger, this feature needs to be turned off. For this purpose, line 46 of the Makefile was changed to LINKER_SCRIPT := cycloneV-dk-ram.ld.
Telnet Connection
Now, let's try connecting to OpenOCD using telnet. With a telnet client, one can directly execute commands supported by OpenOCD6. Additionally, a TCL interpreter called Jim-Tcl runs as the command-line interface, enabling the execution of TCL scripts.
First, ensure that OpenOCD is running. By default, OpenOCD's telnet server waits for connections on port 4444.
The following image shows an example using Tera Term as the Telnet client. To start, configure the settings as shown in the figure: Host: localhost, Service: Telnet, TCP port#: 4444, and click "OK".
After a few seconds, if you see text output from OpenOCD and a prompt for command input, the connection is successful.
Open On-Chip Debugger
>
Simultaneously, the following log should be added to the Shell window where OpenOCD is running.
Info : accepting 'telnet' connection on tcp/4444
Next, here's an example of executing three OpenOCD commands related to CPU debugging (halt, reg, mdw).
> # Halt CPU
> halt
cvsoc.cpu.0 rev 0, partnum c09, arch f, variant 3, implementor 41
target halted in ARM state due to debug-request, current mode: Supervisor
cpsr: 0x600f0153 pc: 0x00101fac
MMU: disabled, D-Cache: disabled, I-Cache: enabled
>
>
> # print registers
> reg
===== ARM registers
(0) r0 (/32): 0x3fffdfa4 (dirty)
(1) r1 (/32): 0x3fffd300 (dirty)
(2) r2 (/32): 0x00000200
(3) r3 (/32): 0x00000000
(4) r4 (/32): 0x00000000
(5) r5 (/32): 0x00000000
(6) r6 (/32): 0x00000076
(7) r7 (/32): 0xfffff014
(8) r8 (/32): 0xffffffff
(9) r9 (/32): 0x00000005
(10) r10 (/32): 0xffd02000
(11) r11 (/32): 0x3fffd2ec
(12) r12 (/32): 0xffffffff
(13) sp_usr (/32)
(14) lr_usr (/32)
(15) pc (/32): 0x00101fac
(16) r8_fiq (/32)
(17) r9_fiq (/32)
...[omitted for brevity]...
(73) d29 (/64)
(74) d30 (/64
>
> # Read a memory mapped register
> mdw 0xffd05014
0xffd05014: 01b6c035
Additionally, let's check other OpenOCD commands such as ```scan_chain``` and ```dap info```.
> scan_chain
TapName Enabled IdCode Expected IrLen IrCap IrMask
-- ------------------- -------- ---------- ---------- ----- ----- ------
0 cvsoc.cpu Y 0x4ba00477 0x4ba00477 4 0x01 0x03
1 auto0.tap Y 0x02d020dd 0x00000000 10 0x01 0x03
> dap info
DAP transaction stalled (WAIT) - slowing down
AP ID register 0x24770002
Type is MEM-AP APB
MEM-AP BASE 0x80000000
ROM table in legacy format
Component base address 0x80000000
Peripheral ID 0x00000ee001
Designer is 0x0ee, Altera
Part is 0x1, Unrecognized
Component class is 0x1, ROM table
MEMTYPE system memory not present: dedicated debug bus
ROMTABLE[0x0] = 0x1003
Component base address 0x80001000
Peripheral ID 0x04001bb961
Designer is 0x4bb, ARM Ltd
Part is 0x961, CoreSight TMC (Trace Memory Controller)
Component class is 0x9, CoreSight component
Type is 0x32, Trace Link, FIFO, buffer
...[omitted for brevity]...
[L01] ROMTABLE[0x20] = 0x0
[L01] End of ROM table
ROMTABLE[0x24] = 0x0
End of ROM table
>
The dap info command displays a list of the contents of the Arm CoreSight DAP's ROM table.
Downloading and Running the Preloader/Baremetal App
A TCL script has been written to download and run both the preloader and a baremetal application. As noted in the file's comments, unlike with gdb, one needs to determine the symbol-to-address mapping in advance7. Once saved as 'download_preloader_app.tcl', it can be executed from the OpenOCD prompt in the telnet terminal using source download_preloader_app.tcl. Make sure to adjust the parts enclosed in […] to fit your environment. Note that if a relative path is specified for the file path, it should be relative to the current working directory of the Shell where OpenOCD is launched.
Similarly to gdb, before executing through the telnet connection, restart the DE10-Nano board5 and restart OpenOCD.
halt
###################################################################
# Download the Preloader
# Specify using a relative path from the pwd of the shell where OpenOCD was launched.
load_image [path to preloader's elf file]
###################################################################
# Setting the Start Address for Execution
reg pc 0xffff0000
###################################################################
# Set a breakpoint at the spl_boot_device function in the preloader
# Example of how to find this address:
# $ arm-altera-eabi-readelf.exe -s [path to preloader elf file] | grep spl_boot_device
#
bp [address of spl_boot_device function] 2 hw
###################################################################
# Execute the preloader
resume
wait_halt
###################################################################
# Reset the WatchDog Timer
set permodrst 0xffd05014
set permodrst_val "0x"[lindex [mdw $permodrst] 1]
mww $permodrst [expr ($permodrst_val)|(1<<6)]
mww $permodrst $permodrst_val
###################################################################
# Load the Baremetal Application
load_image [path to application elf]
###################################################################
# How to find the start address of the application
# (for SOCEDS bundled Altera-SoCFPGA-HardwareLib-16550-CV-GNU)
# arm-altera-eabi-readelf.exe -s [path to application elf] | grep _start
reg pc [start address of application]
###################################################################
# Clear Thumb2 Mode
# cpsr bit-5 : Thumb execution state bit - to be cleared
set cpsr_val [lindex [reg cpsr] 2]
reg cpsr [expr ($cpsr_val)&(~(1<<5)&0xffffffff)]
###################################################################
# Execute the application
resume
Summary
It has been confirmed that with OpenOCD included in QuartusPro v21.3, code download and execution to the Arm Cortex-A9 CPU of Cyclone V SoC is possible via gdb and telnet connections.
It's now feasible to perform JTAG Debugging for Intel SoC FPGAs, which previously required a paid license, with free tools.
Of course, paid debuggers excel in terms of code download speed and GUI environment8.
While "official documentation support is still anticipated," it is hoped that when the support documents are released, there will be improvements in usability and enhanced features.
Postscript
Although the name OpenOCD was somewhat familiar, it had not been used until now. However, the opportunity arose with the inclusion of precompiled binaries in the tool, prompting an early trial.
First impressions are:
- JTAG debugging with gdb is convenient and straightforward.
- Telnet connection looks promising for various operations around JTAG. It also seems convenient when combined with Tera Term's macros.
- The source code is also available on GitHub (see References), which could be interesting for enthusiasts.
That's the general feeling.
Thank you. (Comments and feedback are welcome!)
References
- Open On-Chip Debugger official site
- Link to intel/aji_openocd on GitHub
- Link to intel/libaji_client on GitHub
- Installation and Hello World execution for Nios® V processor
- Boot, simulation, and debugging for Nios® V processor
- Attempted porting of an existing NiosR II/e system to NiosR V/m
Notices & Disclaimers
Intel technologies may require enabled hardware, software, or service activation.
No product or component can be absolutely secure.
Your costs and results may vary.
© Intel Corporation. Intel, the Intel logo, and other Intel marks are trademarks of Intel Corporation or its subsidiaries. Other names and brands may be claimed as the property of others.
The products described may contain design defects or errors known as errata which may cause the product to deviate from published specifications. Current characterized errata are available on request.
Intel disclaims all express and implied warranties, including without limitation, the implied warranties of merchantability, fitness for a particular purpose, and non-infringement, as well as any warranty arising from the course of performance, course of dealing, or usage in trade.
While QuartusPro v21.3 does not support this device, it was challenged due to the desire to see it operate on a reasonably priced FPGA. ↩︎
From the official website's What is OpenOCD section. ↩︎
Even without this description, if the FPGA is not configured, it will operate by automatically detecting the dbgbase address at startup. The address detected automatically was displayed as Detected core 0 dbgbase: 80110000 when the debug option (-d) was used. On the other hand, if an IP (SLD Node) for JTAG is configured in the FPGA, automatic detection does not work well, and without this option, a startup error occurs. ↩︎
With recent versions of Windows, the make of the preloader may result in an error. One countermeasure is to set /usr/bin at the beginning of the PATH environment variable with export PATH=/usr/bin:$PATH. ↩︎
Since a CPU reset command has not been found, manual resetting of the target is currently used as a substitute. ↩︎ ↩︎
For detailed commands, refer to the OpenOCD User’s Guide. Not all commands are implemented. ↩︎
If anyone knows a better way, please share in the comments m(–)m ↩︎
Combining with VSCode or Eclipse might be possible for self-assembly. Using VSCode+gdb+OpenOCD for ARM development can be a reference. ↩︎
Link Copied
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Printer Friendly Page